Employee theft has long plagued the restaurant industry for decades, costing operators billions in losses each year. In fact, according to the National Restaurant Association, employee theft accounts for 75% of inventory shortages and 4% of restaurant sales, making it a top threat to profitability. Historical accounts show that internal fraud, such as under-reporting sales at the register to sneaking out extra inventory, remains a constant threat to a restaurant’s finances. Even iconic spots like Nathan’s Famous in New York, best known for its century-long hot dog tradition in Coney Island, have faced large-scale employee fraud. A CPA Journal report titled “Fighting Fraud and Serving Famous Frankfurters for Over a Century” details how Nathan’s uncovered unauthorized transactions and inventory discrepancies.
As restaurant operators roll out loyalty programs, contactless payments, and automated inventory systems, criminals adjust their tactics just as fast. In 2023, a general manager at Mancino’s Pizza and Grinders was convicted of embezzling $130,000 from the customer loyalty program.
Recently, a North Carolina police department published an alert asking customers using restaurant drive-thrus to use cash or digital payment apps instead of credit or debit cards. The reason—Restaurant employees were taking photographs of customer cards for later use!

Every innovation to streamline restaurant operations and improve customer service opens up new possibilities for internal theft. The table below summarizes the most common threats restaurants should watch out for.
- Credit card manipulation- Cash skimming
- Theft of premium inventory (alcohol, specialty items)
- Time and payroll fraud
- Cash skimming and register voids
- Loyalty program manipulations
- Inventory theft (ingredients, supplies)
- Payroll padding
- Cash theft (register voids, fake refunds)
- Loyalty program fraud
- Digital payment scams
- Time theft and buddy punching
- Inventory theft (liquor, beer)
- Unauthorized discounts/free drinks
- Cash skimming
- Inflated waste reports
- Cash skimming
- Ingredient and inventory theft
- Misreporting sales figures
- Time theft (payroll fraud)
- Digital payment manipulation
- Inventory fraud (falsified usage)
- Loyalty and rewards fraud
- Payroll manipulation
- Inventory theft (bulk food)
- Cash skimming
- Payroll and timecard manipulation (buddy punching)
- False reporting of waste
In this post, we’ll explore widely prevalent frauds and ingenious methods used by unscrupulous employees to make a fast buck at the expense of your bottom line. You’ll see how classic tactics like skimming and falsifying inventory records combine with new threats such as loyalty program abuse and digital payment scams. We’ll also highlight the latest technology and best practices so you can defend your profits without destroying trust in your team.
Types of Internal Theft in Restaurants and Mitigation Strategies
1. Cash Register & Refund Fraud
Cash skimming, bogus refunds, after‑hours voids, and “no‑sale” drawer pops let employees walk away with real money while the POS report still appears to balance. Because margins in food service are thin, even a single dishonest cashier can erase a week’s profit.
These cases show how easily register fraud can hide inside daily reports when independent controls are missing. So, how do you stop it? Combine technology and process to close every loophole.
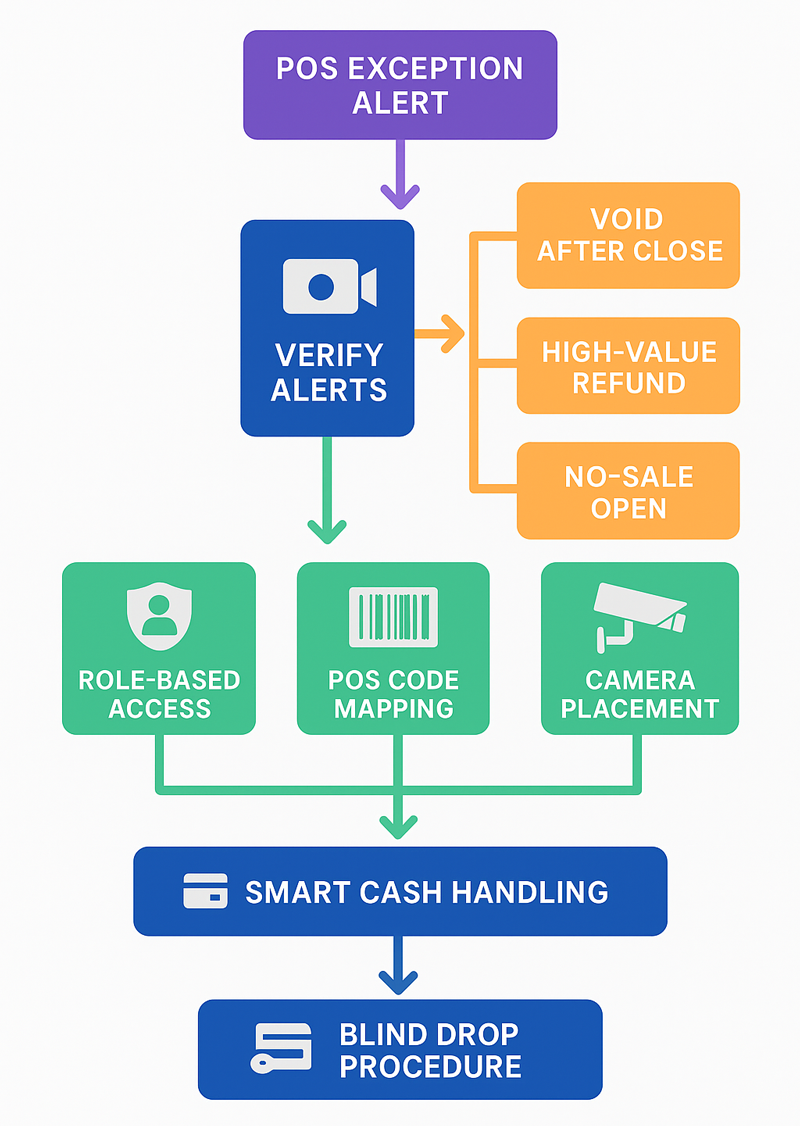
POS Exception Reporting and Role‑Based Controls
Millions of POS transactions can be analyzed to detect unusual transactions and uncover potential fraud. POS exception reporting can flag instances of voids after close, high‑value refunds, frequent “no‑sale” opens, repeated cancelled items, and large manual discounts. Interface Systems’ POS exception reporting links each alert to a matching video clip, allowing managers to review incidents within seconds.
POS exception alerts, such as voids after close or high-value refunds, are flagged and linked to security video for quick review.
When implementing exception reporting, restaurant chains should watch for these common challenges:
- Implement Role-Based POS Access: Exception reports work best if only authorized managers can perform high-risk actions. Use tools like fingerprint or face scan logins to tie every void, comp, or refund to an individual. Also, implement blind closeouts so cashiers can’t adjust totals to hide shortages.
- Map Product Codes Accurately: A key challenge during setup is mapping POS codes correctly. When a restaurant chain lumps three discount codes, such as DISC10 (manager override), DISC10_BDAY (server birthday comp), and DISC10_AUTO (automatic happy‑hour), into a single “10 Percent Discount” category, the system floods managers with false alerts while hiding real cash‑ticket voids. Restaurants should hold data‑mapping workshops with the implementation partner, focus on the most important metrics first, and refine exception triggers every quarter so managers are not swamped with noise.
- Ensure Video Recording is Usable: Security cameras may need to be upgraded or repositioned so they capture every transaction for accurate verification.
Intelligent Cash Drawers (Smart Tills) and Blind Drops
Smart tills weigh bills and coins after each sale and reconcile the result with the POS in real time, so shortages surface before the shift ends. APG Cash Drawer’s SmartTill pilots claim to show a significant reduction in unexplained cash loss.
Blind drops add a manual safeguard. Cashiers close out without seeing the expected total, and a second employee or supervisor verifies the deposit. Pairing blind drops with smart tills reduces reconciliation time, deters collusion, and eliminates lone‑wolf counting errors.
Because smart tills are expensive, pilot them in the highest‑cash locations first and require each cashier to sign in so every transaction ties to an individual, not a shift.
2. Inventory Theft & Waste Falsification
Pilfered steaks, “mistake” entrees slid into backpacks, and padded waste logs drain profit just as fast as cash theft. With food costs already around 30% of sales for many restaurants, a few phantom cases of tenderloin or a doctored spoilage log can wipe out a week’s margin.
Two employees at a Pennsylvania Arby’s were arrested after hiding ~$3500 in roast beef in trash bags and hauling it away after hours.
These cases show how easily food disappears when inventory controls rely on trust alone. So, how do you stop it? The solutions below blend technology and procedure to plug every leak.
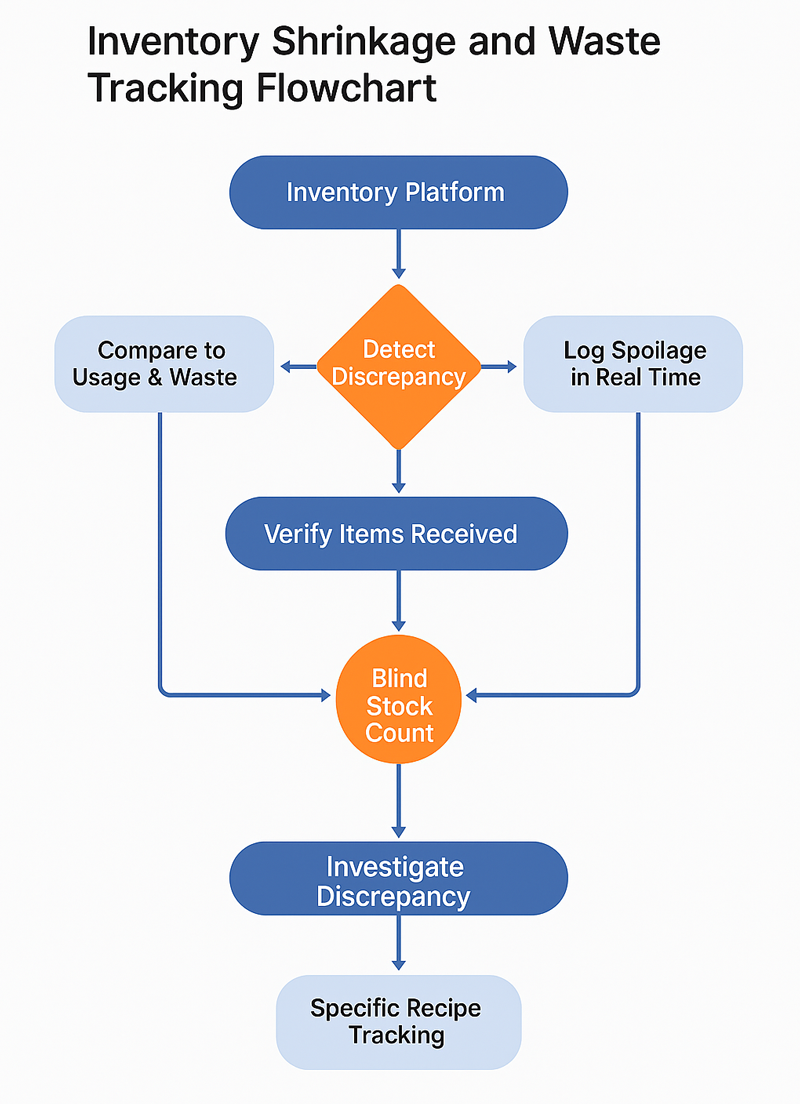
Real‑Time Inventory Analytics & Waste Tracking
Modern inventory management platforms (e.g., Toast’s xtraCHEF or CrunchTime) compare theoretical stock vs. actual usage, flagging anomalies like a spike in high‑value meats or sudden waste surges. For example, xtraCHEF can prompt staff to log each spoilage event immediately, turning waste into searchable data.
When rolling out inventory analytics, restaurant chains should watch for these common challenges:
- Capture accurate recipes and portions: Without precise yields, “expected” usage is guesswork. Start with top‑cost items, weigh every trim, and update recipes quarterly.
- Log waste immediately: Staff forget end‑of‑shift forms. Use the app on a kitchen tablet so cooks tap a button as waste occurs, or the data will be worthless.
- Verify vendor deliveries: Short shipments (fewer items delivered by the vendor) look like theft on reports, as the POS is expecting a larger quantity in the inventory. Pair inventory software with two‑person receiving and photo capture of invoices so variances trace back to suppliers, not staff.
Surprise Stock Counts & Camera‑Aided Audits
Unannounced counts backed by overhead cameras and time‑stamped video add human pressure and visual proof. Managers pick a shelf, count six items, compare them to the system, and review footage when numbers clash.
Blind counts, where the counter does not know the theoretical total, remove the temptation to “adjust” tallies. Coupled with analytics, these spot checks deter theft, expose waste padding, and confirm that perpetual inventory numbers match physical reality.
Start your surprise counts where theft and spoilage hit hardest, such as places that store the most valuable or easily pilfered items, like the liquor cage or the walk-in cooler. Use these high-risk areas to fine-tune the counting routine, camera angles, and variance workflows. Once the method runs smoothly and staff know exactly what to do, expand the same process to every other storage area across the chain.
3. Payroll Fraud & Timecard Abuse
Inflated timecards sap labor budgets just as fast as a light-fingered cashier drains the till. According to the American Payroll Association, time theft affects about 75% of US businesses. These phantom hours stack up quickly in restaurants where labor already runs near 30 percent of sales.
Time theft flourishes when punches are easy to fake and shift records go unchecked. How can restaurants stop time theft? The solution is to pair identity verification with airtight time-tracking audits.
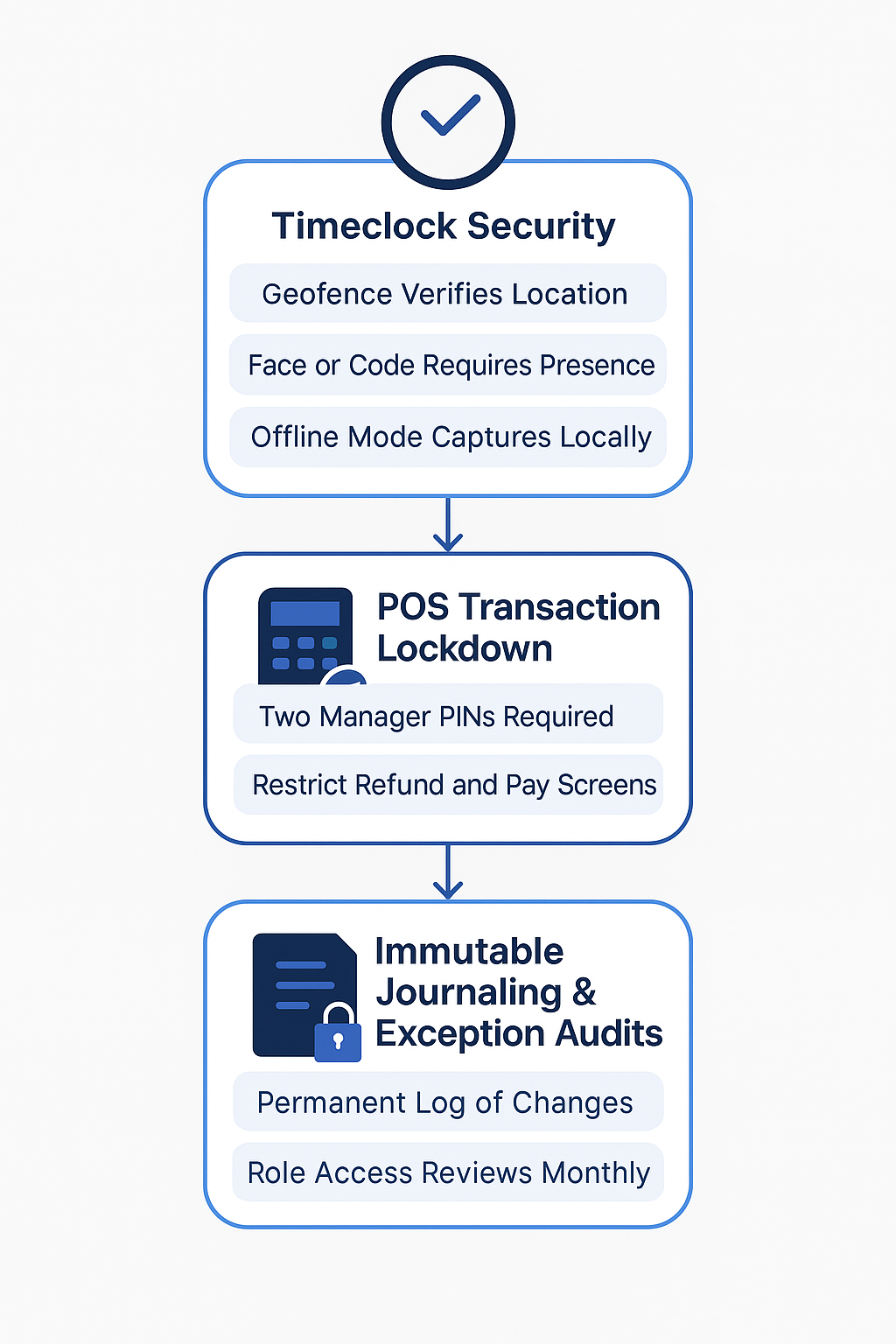
Biometric Time Clocks & Geofenced Clock-ins
Modern clocks now confirm who is clocking in and where they are standing before a shift can start. Deputy’s tablet kiosk snaps a live photo, matches it to the employee record, and accepts the punch only when the faces align. When I Work achieves the same goal with GPS: its mobile app allows a punch only if the phone sits inside a tight geofence that hugs the restaurant’s four walls. By validating identity and location in real time, both systems cut off buddy punching, early clock-ins, and end-of-shift padding before those extra minutes ever land in payroll.
When rolling out biometric and geofence clocks, restaurant chains should watch for these common challenges:
- Train staff on privacy: Employees may worry about face scans or GPS tracking. Provide a short orientation, post clear data-use notices right beside the clock, and program the system to purge images every 30 days. Explain that images are only stored short-term for verification, to reduce pushback.
- Set the right radius: A 300-foot geofence can reject valid punches in a mall food court or multi-tenant complex. Walk the site with a test phone at open and close, map any dead spots, and include service corridors used by the staff to enter the premises. Once location drift stays under 30 feet, tighten the zone so only on-premise punches clear.
- Provide an offline fallback: Internet drops happen. Enable a PIN or QR-code kiosk mode that encrypts punches locally, time-stamps them, and syncs as soon as Wi-Fi returns. Without this safety valve, managers can override the clock whenever there is a network hiccup.
Labor-Audit Analytics & Surprise Shift Checks
Most contemporary time and scheduling platforms compare planned shifts to actual punches, flagging early clock-ins, unapproved breaks, and double shifts. Managers can filter a “punch audit” report and approve payroll in minutes.
Blind spot checks add human pressure. A supervisor shows up unannounced, cross-references on-floor headcount with live clock-ins, and initials the report. Start with weekends when time theft peaks as senior managers are off and expand chain-wide once the routine is smooth.
Common challenges include:
- Photo verification gaps. Some staff cover the tablet camera. Mount the device at eye level and enable automatic photo capture so faces stay in frame.
- Schedule drift. If managers edit shifts after the fact, audits lose value. Lock schedules at midnight the day before and require approval notes for any change.
- Data overload. Weekly punch reports can run into tens of pages. Filter by “late clock-in over five minutes” or “unmatched break,” then review the top ten offenders first.
By combining biometric punches, geofenced locations, automated audits, and spot inspections, you cut phantom hours before they inflate payroll.
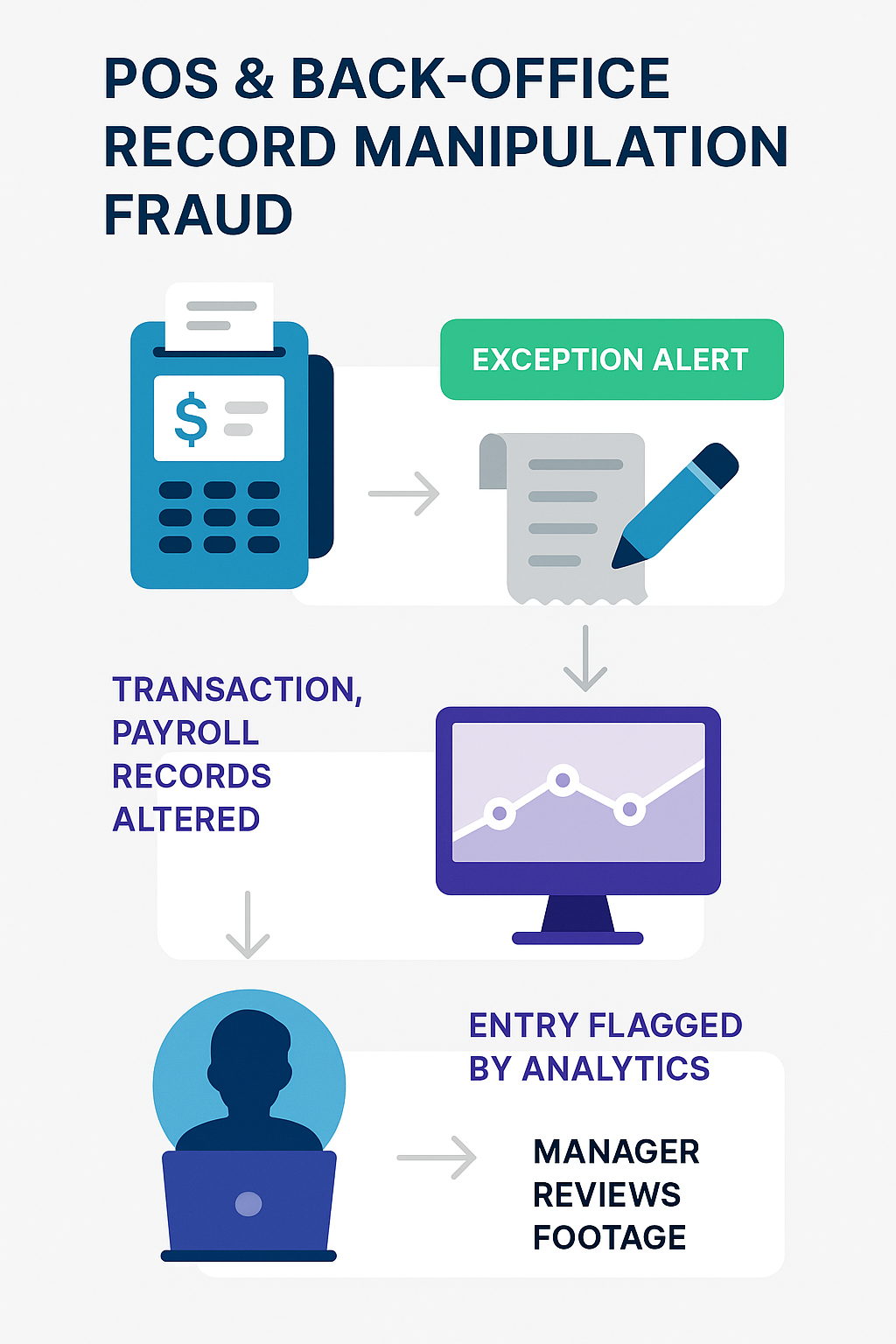
4. POS & Back‑Office Record Manipulation Fraud
Employees (and occasionally outsiders) can edit sales records, alter discount rules, or push fake refunds straight from the back office, wiping all evidence of earlier theft. According to IBM, restaurant chains are victims of sophisticated email and POS vulnerability exploitation due to the relatively low cybersecurity awareness among staff and the high employee turnover.
Police arrested two shift managers after an internal audit showed they voided dozens of settled cash tickets hours after the sales, then pocketed the money. Investigators say one manager stole more than $40,000 over 18 months, while a second manager siphoned another $9,000 using the same back-office void screen.
These incidents prove that, once someone secures back-office credentials, every other control can be erased with a few keystrokes. So, how do you shut the door? The fixes below combine tamper-proof logs with ironclad access rules.
Immutable Transaction Logs & Exception Alerts
Modern POS suites such as Oracle Simphony and PAR Tech Detect hash each transaction, store it in a write-once log, and trigger an alert if anyone reopens, deletes, or re-settles a ticket. Managers receive a dashboard highlighting late-night edits, refunds over a preset limit, or changes from an unrecognised back-office PC. Here are some of the practical challenges to watch:
- Storage bloat: Immutable journals grow fast; archive to low-cost cloud storage every 90 days. Rotate off-site backups after a year to keep the local database lean and query speeds high.
- Alert fatigue: Start with simple rules such as after-close ticket opens, refunds over $250, and price edits above 20 percent. Then expand once baseline traffic is known. Review trigger hit rates monthly and retire rules that deliver less than a 5 percent true-positive rate.
- Video sync Link each flagged ticket to camera footage so investigators can verify intent in seconds. Keep POS and recorder clocks synced daily; even a two-minute drift makes reconciling data with video painful.
Least-Privilege Access & Dual-Approval Overrides
Platforms like NCR Aloha let operators assign granular rights (e.g., refund limit $50) and force a second manager’s PIN for high-risk tasks such as price-table edits or bulk gift-card loads. Multi-factor authentication (SMS codes or FIDO keys) blocks ex-employees who try stale credentials. Here are some pitfalls to watch for:
- Role creep: Managers collect extra permissions over time. Run quarterly access reviews and reset to template roles. Document each change request so you can trace why an extra right was granted and ensure it still makes business sense.
- Shared passwords: Kill generic “admin” accounts; require named IDs so audit trails always point to a person. Enforcing unique credentials also lets you disable a single departing employee without breaking the entire back-office login.
- Emergency mode: If dual approval jams during peak hours (when one of the staff members is not available to approve the override), staff will bypass the system. Create an “override token” that logs every use and expires in 15 minutes. Store those override events in a separate report so upper management can audit every incident and spot patterns of abuse.
By hard-locking transaction history and enforcing least-privilege, you ensure any ticket change leaves a forensic trail and any thief leaves empty-handed.
5. Customer Payment & Loyalty Program Exploits
Refunds to an employee’s card, loyalty points quietly moved into a manager’s account, and blank gift cards activated off the books can drain revenue without touching the cash drawer. According to Paytronix, nearly 49000 cases of gift card fraud in 2022 cost victims over $228 million.
Michigan State Police charged longtime general manager James Lake with embezzling about $130,000 by back-entering fake reward redemptions on a single office computer, then pulling matching cash from the tills. Investigators linked ninety-nine percent of all reward adjustments to that machine.
These types of fraud flourish when refund screens have no oversight and loyalty programs lack proper controls. The measures below introduce tighter permissions and automated monitoring to catch issues early.
Real-Time Refund Holds & Dual Approvals
Payment gateways such as Adyen and Stripe’s Radar let operators cap refund amounts, flag card mismatches, and hold any refund that exceeds the limit in a pending queue. The money does not leave the merchant account until a supervisor reviews the receipt, checks the video, and approves the transaction with a second PIN.
A note of caution – staff need clear training on how to release or deny pending refunds; otherwise, the queue backs up during peak periods.
Loyalty-Fraud Analytics & Multi-Factor Authentication
Platforms including Punchh and Paytronix score every redemption against purchase history, device ID, and location. Suspicious spikes trigger an instant review, and multifactor login keeps hijacked accounts from draining points overnight.
Orphaned accounts attract thieves. Prompt guests to update their email and phone numbers twice a year so inactive profiles are less vulnerable to takeover.
Gift Card Activation Locks & Daily Reconciliation
NCR Aloha and Lightspeed let only corporate users activate batches of gift cards and prompt for a manager PIN whenever a single card exceeds a configurable limit (often set at fifty dollars). Run a nightly “sold versus activated” report so any missing card numbers appear within twenty-four hours.
Layering real-time refund holds, loyalty analytics, and strict gift-card rules helps restaurants stop digital dollars from leaking before customers or finance can raise the alarm.
6. Data Security Breaches by Insiders
When employees retain broad back‑office credentials or fail to log out of POS and admin systems, they can become an easy path for a data breach. In the 2024 Verizon Data Breach Investigations Report, malicious insiders were responsible for 9% of data breaches, and stolen credentials accounted for 50% of the data compromised.
A former menu production manager at Walt Disney World, Florida, was arrested for violating the Computer Fraud and Abuse Act by hacking into Disney’s restaurant menu database and making unauthorized changes to menu configurations.
Once an insider has improper access, even the strongest perimeter defenses cannot stop them. The controls below combine least‑privilege access, endpoint restrictions, real‑time monitoring, and targeted training to prevent breaches before they happen.
Privileged Access Management and Credential Hygiene
Use platforms like CyberArk or BeyondTrust to grant elevated rights only when needed. Access requests require manager approval, and every action is logged with user, time, and scope.
Stale accounts linger – schedule monthly access reviews and auto‑disable any login unused for 30 days to kill orphan credentials.
Endpoint Lockdown and Application Whitelisting
Lock down POS terminals and back‑office PCs using tools like Carbon Black or Microsoft AppLocker, so that only approved applications can run. Prevent unauthorized software installs via email or USB. Configure alerts for any new executable detected, and block USB ports to stop rogue devices.
Some of the common loopholes that restaurants need to plug include app installs via emails or USB devices. Configure the system to generate alerts when new apps are detected, block USB ports, and quarantine unfamiliar files immediately.
Security Awareness & Insider‑Threat Training
Platforms such as KnowBe4 and Proofpoint run ongoing simulated attacks, micro‑learning modules, and gamified quizzes. They track individual risk scores, enforce refresher training, and include features for real‑time reporting.
The biggest challenge that restaurants should watch for is passive compliance. Replace passive “check‑the‑box” learning and long videos with short, interactive workflows that require employees to actively identify red flags and practice reporting incidents. Use scenario‑based drills, and closely coach any repeat offenders (those flagged by the training platform’s analytics) before they become liabilities.
By combining strict access controls, endpoint restrictions, and continuous employee engagement, restaurants can stop insider‑driven breaches before customer data or payment credentials are compromised.
7. AI‑Assisted Fraud & Automation
Fraudsters can now use generative Artificial Intelligence (AI) bots to carry out hundreds of suspect refunds or loyalty-point redemptions in seconds, then hide their tracks among thousands of legitimate transactions.
According to the Association of Certified Fraud Examiners, fraudsters can leverage AI to automate large-scale scams and even use AI-generated misinformation to evade traditional rule-based fraud controls.
Restaurant chains are especially at risk when they deploy robotic process automation (RPA) for tasks like order taking, menu updates, or inventory reconciliation without proper oversight. The same scripts can be hijacked or repurposed to run refund scams or synthetic transaction attacks on loyalty programs.
Machine Learning Anomaly Detection & Behavioral Analytics
Platforms such as Stripe Radar and Forter apply supervised and unsupervised models to every sale, profiling normal patterns per cashier, per site. They surface clusters of minute automated refunds, out-of-pattern device usage, or loyalty-drain scripts that slip past static rules.
Watch out for these implementation challenges:
- Data Integration & Quality Fraud models rely on accurate, complete data from every POS terminal, loyalty system, and e-commerce touchpoint. If fields are truncated, timestamps are lost, or device IDs are mislabelled, the platforms cannot learn your true transaction patterns. Before go-live, run end-to-end test transactions from each location, device, and promotion type to confirm that every attribute is properly fed to the fraud detection engine.
- False-Positive Tuning: Out-of-the-box settings err on the side of caution, flagging legitimate rush-hour refunds or bulk loyalty redemptions as fraud. Without early tuning, your operations team will drown in alerts. Build a two-week “quiet launch” period during which you review alerts in bulk, adjust threshold settings, and whitelist known-good patterns, such as daily happy-hour voids, before enforcing blocks.
- Performance & Latency: Real-time scoring adds network calls and model inference time, which can introduce milliseconds of delay at checkout. In high-volume restaurants, even small lags translate into longer lines and frustrated guests. Work with your vendor to benchmark response times under peak loads and configure a “fast-path” fallback that temporarily whitelists transactions if the API call exceeds 300 ms.
- Explainability & Auditability: Both Stripe Radar and Forter return risk scores and high-level reasons (“velocity anomaly,” “device mismatch”) but do not expose raw model logic. When finance or compliance teams demand details, you will need to supplement with your exception logs and human-readable rationale. Set up a parallel audit trail that captures transaction metadata, alert triggers, and reviewer notes for every blocked or flagged event.
- Cost Management & Volume Control:Fraud-scoring fees scale with transaction volume. A sudden spike, such as holiday bulk orders or network retries, can inflate your monthly bill. Monitor your scoring counts in real time, set budget alerts, and negotiate rate caps or volume-based discounts with your vendor. For predictable savings, batch low-risk transactions into periodic scoring windows rather than scoring every transaction immediately.
Conclusion
Employee theft isn’t just a financial drain. It’s a systems failure. From cash skimming and bogus refunds to loyalty program fraud and falsified timecards, the cost of internal theft adds up fast. Restaurants already run on tight margins. A single trusted employee exploiting a back-office screen or POS loophole can wipe out an entire week’s profit.
While this article outlines strategies that combine technology and process to prevent internal fraud before it happens, no technology can replace human needs or desires. When employees feel undervalued or treated unfairly, they may end up taking shortcuts. A strong defense combines controls with culture. That means fair pay, clear expectations, consistent training, and visible recognition for doing the right thing. When employees trust leadership and understand the rules, most will follow them and help protect the business, too.
Combining hard systems with soft accountability builds a restaurant environment where theft is both harder to pull off and less tempting to try. That’s the real goal: not just fewer losses, but a workplace where trust, transparency, and profitability can coexist.




