Managed Intrusion Alarm System to Secure Multi-Location Business
Upgrade to the next generation of managed alarm services with TamperShield™ technology to detect criminal interference of alarm panels and stop break-ins. Easily manage multi-site alarm operations from any browser-based device.

Trusted by






Managed Intrusion Alarm Can Help You Avoid These Common Issues
Cumbersome Vendor Management
Multi-site businesses struggle to manage intrusion alarm vendor sprawl. Too many alarm vendors create significant operational overheads for loss prevention teams. Managing invoices, price escalations, and contracts can suck away precious time from dealing with new and emerging threats across locations.
Inconsistent Processes
Every alarm vendor in the mix brings in their own alarm maintenance and escalation process. Inconsistent SLAs at different locations create operational challenges and put people and inventory at risk. Training employees can become challenging when employees are deployed to new locations.
Unfavorable ROI
Multi-location businesses saddled with a mix of legacy and new intrusion alarm devices incur significantly higher maintenance costs as they neither have the ability to leverage scale nor the option to deploy advanced solutions.
Leverage A Wide Variety Of Intrusion Sensors
Our security experts can design a customized alarm monitoring solution to tackle a wide variety of indoor, outdoor, and environmental security risks.

Door and Window Contact Sensors

Motion Detectors

Glassbreak Detectors

Vibration Sensors

Specialty Sensors

Panic Buttons or Key Fobs
Offer employees the option to discreetly seek assistance using emergency panic buttons that can either be fixed or available as key fobs.

TamperShield: Detect Alarm Tampering Before Break-Ins
Deploy our TamperShield alarm monitoring technology to perform automated health checks on the alarm panel communicators at all your locations. Our iSOC can spot line cuts, cellular jamming or other alarm panel tamper attempts within minutes, thereby enabling faster threat response. TamperShield is designed for businesses that cannot afford to let their guard down.
- Finds network issues, communication failures, and alarm tampering within minutes
- Alerts iSOC for rapid response and enhanced safety
- Currently compatible with DMP and Honeywell panels
Remotely Manage Alarm System from Any Connected Device
Get remote alarm management capabilities with enterprise-grade administration features. Easily manage multi-site alarm operations from any browser-based device.
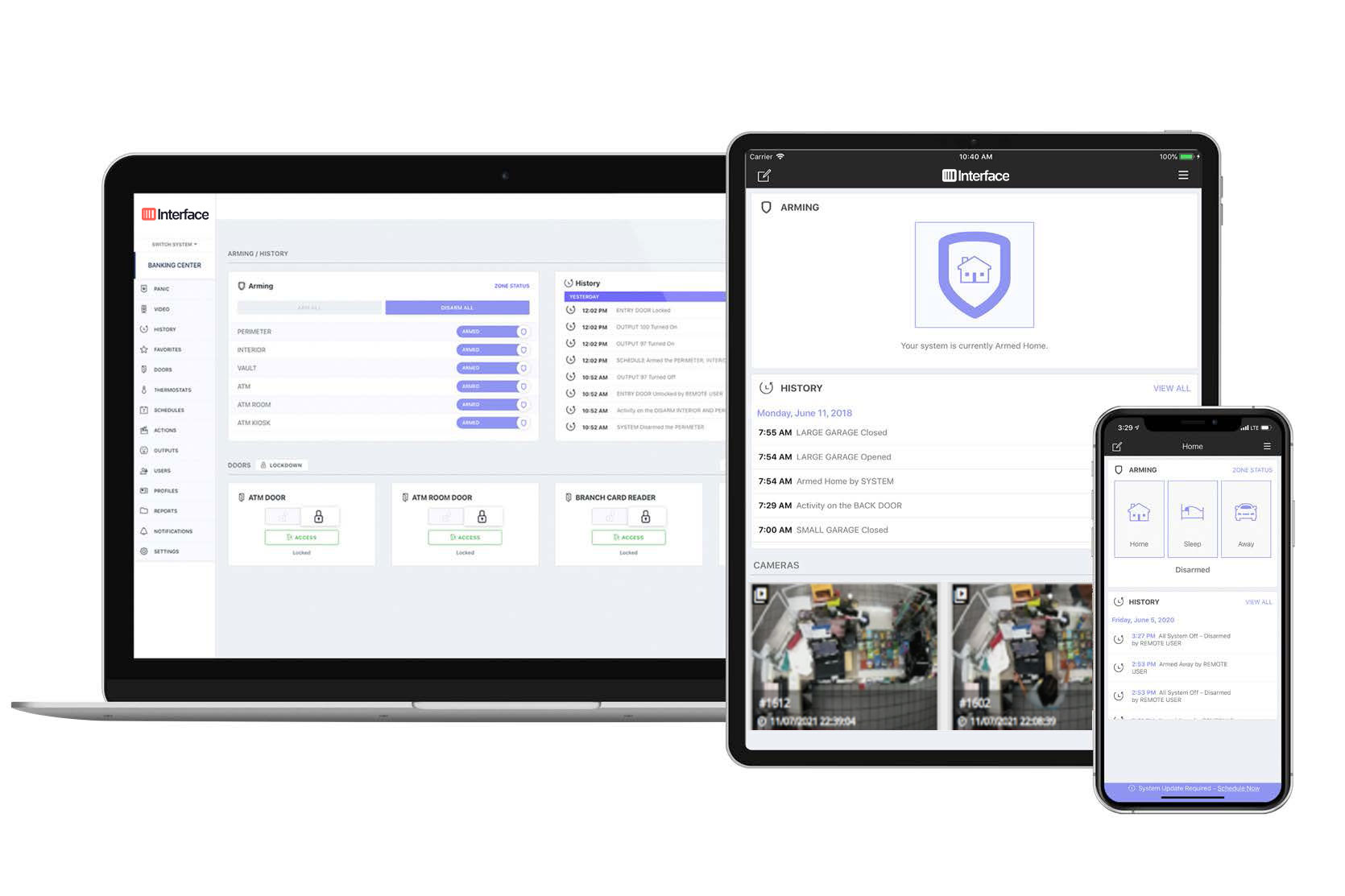
Manage Zone Status, Arm/Disarm Alarms
Remotely view all faulted zones and take action. Arm or disarm alarms or pre-defined alarm areas so access is provided only where it is needed.
Get Notifications and Alerts
Enable customized notifications for alarms, sensor activity, arming/ disarming or alarms or zone trips in sensitive areas where high-value inventory is stored.
Multi-Site User Administration
Easily add, edit, or delete users remotely. Map user schedules and profiles to a set of alarm systems at any number of locations.
Assign Granular User Roles and Rights
Edit alarm access code for any user, create temporary alarm codes for users with pre-defined expiry and assign authority levels (Example, ‘arm only’)
Let Users Manage Contacts and Passcodes
Users can manage their own routine system tests or change emergency contact lists and verbal passcodes. Changes are automatically synced with the monitoring center.
Access Comprehensive Reports
View historical data on all alarm events and sensor activities. Create reports and automatically email reports based on a schedule.
Why You Should Switch to a Managed Intrusion Alarm System
- Evaluate security needs based on the type of locations and risks
- Understand the scope of the security needs
- Assess for common security vulnerabilities
- Review regulatory requirements
- Understand capabilities of legacy alarm systems
- Define current & future security needs
- Review past maintenance issues
- Document integration requirements
- Map requirements to intrusion alarm devices
- Identify alarm design templates
- Finalize alarm system platform
- Create bill of materials
- Install alarm devices
- Set up alarm connectivity
- Create alarm system SOPs
- Train customer teams
- Integrate alarms with video surveillance and/or access control systems and other Interface Managed Services
- Conduct remote alarm monitoring
- Enable reporting and notifications
- Create ongoing maintenance plan
- Perform periodic inspections
- Optimize alarm SLAs
- Review false alarm mitigation
We Partner with Leading Intrusion Detection Technology Companies
Interface can design a turnkey managed intrusion alarm solution by seamlessly bringing together in-house design and monitoring expertise and leveraging next-generation hardware and software solutions offered by our partners.

Digital Monitoring Products (DMP) Intrusion Devices

Honeywell Pro-Watch
Leverage Alarm Integrations to Improve Security
Uncover Security Insights
Combine alarm events with video from security cameras and access control systems to gain granular insights on security events.
Enhance Deterrence
Use alarm events as triggers to activate facility lighting to deter potential intruders. Integrate alarm sensors to initiate local announcements or automated remote voice downs during non-business hours.
Verify Alarm Events
Minimize false alarm costs by deploying video-verified alarms that are monitored by Interface’s interactive Security Operation Centers (iSOCs).


El Pollo Loco Relies on Interface’s Managed Alarm Services to Cut False Alarm Costs and Deter Crime
Frequently Asked Questions
An unmonitored intrusion alarm system is a security system that is not connected to a monitoring service. Instead, the alarm is triggered locally, and it relies on the occupants to respond to the alarm and alert the authorities if necessary.
While unmonitored intrusion alarm systems can be less expensive than monitored systems, they do have several disadvantages. Without a monitoring service, there is no guarantee that anyone will respond to the alarm. This can be particularly problematic if the occupants are away from the building (such as during non-business hours) or if the alarm is ignored or mistaken for a false alarm. Additionally, unmonitored systems do not provide any means of remote control, such as arming or disarming the system remotely through a smartphone app or web interface.
Both wireless and hardwired intrusion alarm systems have their advantages and disadvantages.
Advantages of wireless intrusion alarm systems
- Easier and less expensive to install, since they don't require running wires throughout the building.
- More flexible in terms of where sensors can be placed since they don't need to be located near a wired connection.
- Can be easily expanded or modified as needed.
- Can be controlled remotely through a smartphone app or web interface.
- Generally more reliable and secure than in the past, with advanced encryption and anti-jamming features.
Disadvantages of wireless intrusion alarm systems
- Possibly more vulnerable to interference from other wireless devices, such as Wi-Fi routers or cordless phones.
- Batteries powering the wireless sensors will need to be replaced periodically.
- May have a shorter range than hardwired systems, limiting the distance between the sensors and the control panel.
Advantages of hardwired intrusion alarm systems
- More reliable and less prone to interference or signal loss than wireless systems.
- Typically have a longer lifespan than wireless systems.
- Often have more options for sensors and devices to choose from.
- Can be integrated with other hardwired systems, such as fire alarms or access control.
Disadvantages of hardwired intrusion alarm systems
- Can be more expensive to install, since they require running wires throughout the building.
- May require professional installation, adding to the cost.
- Less flexible in terms of where sensors can be placed since they need to be located near a wired connection.
- Harder to modify or expand once installed.
- Power outages or failures can cause the system to fail.
| Alarm Mode | Example |
|---|---|
| All sensors and devices are activated to detect unauthorized entry | A retail store sets the alarm system to Armed Mode after closing for the night |
| Disarmed Mode: The alarm system is turned off and sensors and devices are not activated | A restaurant turns off the alarm system during business hours |
| Stay Mode: Only certain areas of the building are armed while others remain disarmed | A hotel activates Stay Mode in the lobby and public areas during the night while keeping the guest rooms disarmed |
| Instant Mode: The alarm system is immediately activated when a sensor or device is triggered | A bank uses Instant Mode to ensure an immediate response in the event of an intrusion |
| Panic Mode: A panic button or remote is used to trigger the alarm system in case of an emergency | A jewelry store uses Panic Mode in the event of a robbery |
| Test Mode: The alarm system is tested to ensure that all sensors and devices are working correctly | A business runs Test Mode after installing a new sensor to ensure it is functioning properly |
Interface business security teams consider several factors when selecting intrusion alarms for multi-location businesses such as retail chains and restaurants. Here are some of the key considerations:
- Type of Business: The type of business being secured plays a significant role in determining the type of intrusion alarm needed. For example, restaurants may need intrusion alarms to protect against break-ins or theft, but they may also need additional security measures such as temperature monitoring for refrigerators and freezers, fire detection, and water sensors in areas prone to flooding.
- Location: In multi-site businesses, every location has a different risk profile and the level of security coverage needed may vary.
- Size of the Business: The size of the business will also determine the type of alarm system needed. A larger business (for example, big box retailers) may require more advanced features such as multiple zones, while a smaller business may only require basic monitoring.
- Budget: Interface always seeks to balance the need for a high-quality alarm system with the budget constraints of the customer. We avoid the “rip and replace” approach as much as we can.
- Integration with Other Systems: A business may already have other security systems in place, such as CCTV cameras. Therefore, the intrusion alarm must be compatible with these existing systems for seamless integration.
- Scalability: A multi-location business requires a scalable alarm system that can be easily expanded to accommodate growth or changes in the business. For example, when a restaurant adds a drive-thru, they may need to install additional alarms to protect the drive-thru area and also integrate the intercom system with alarms and cameras.
We design our intrusion alarm solutions with redundant communication paths that include wired connectivity and cellular backup, monitor the status of the alarm panel connection to our monitoring systems, with the capability to detect panel power outages. We work with our customers to develop robust processes to ensure that all alarm systems managed by our teams remain functional 24X7, 365 days a year.
We define standard operating procedures for all types of events- arming/disarming of alarms, actual alarm events, and responding to system health or outage notifications as part of our proactive support and maintenance programs.
Bandwidth constraints at the location can potentially impact the performance of managed intrusion alarms, particularly if the alarm system relies on network connectivity for remote monitoring or management.
In a managed intrusion alarm system, the sensors and control panel communicate with a central monitoring station or security company over a network connection, such as broadband internet or cellular data. If the location has limited bandwidth, such as a slow internet connection or poor cellular reception, this can result in slower response times, delayed alerts, or missed alarms. Additionally, some managed intrusion alarm systems may rely on video surveillance or remote access control features, which can place a higher demand on the network connection. If the bandwidth is limited, the video feeds may be lower quality or may experience buffering, and remote access control commands may be delayed or unresponsive.
To mitigate the impact of bandwidth constraints on managed intrusion alarm systems, it's important to choose a system that is optimized for low-bandwidth environments, such as one that uses compression algorithms to reduce the amount of data transmitted over the network. Additionally, it may be helpful to prioritize network traffic for the alarm system, to ensure that it receives sufficient bandwidth even during periods of high network usage.
Interface can design an intrusion alarm solution that takes into consideration existing connectivity challenges. We offer alarm solutions that rely on LTE connectivity either as a backup or as a primary connection to completely bypass bandwidth availability issues. Interface has partnerships with leading wireless carriers in North America and can include bandwidth provisioning as a bundled solution.
A false alarm is an activation of an intrusion alarm system that is not caused by an actual security breach or emergency. False alarms can be triggered by a variety of factors, including user error, equipment malfunction, environmental conditions, or even the presence of animals or insects.
When a false alarm occurs, the response will depend on the specific policies and procedures of the alarm system and the monitoring company. In some cases, the alarm system may simply sound an audible alarm for a set period of time and then reset itself automatically. However, in other cases, the monitoring company may attempt to contact the occupant or designated contact person to confirm whether there is an actual emergency. If the contact person cannot be reached or cannot confirm the emergency, the monitoring company may then dispatch local law enforcement or security personnel to investigate the alarm.
False alarms can have several consequences, including:
- Disturbance to the occupants: False alarms can be disruptive and stressful to occupants, particularly if they occur frequently or at inconvenient times, such as in the middle of the night.
- Wasted resources: False alarms can result in wasted resources, including time and money spent by law enforcement or security personnel responding to the alarm.
- Potential fines or penalties: In some jurisdictions, frequent false alarms can result in fines or penalties for the occupant or property owner, to encourage them to take steps to reduce false alarms.
To avoid false alarms, it's important to ensure that the intrusion alarm system is installed and maintained correctly and that all users are trained on how to operate the system correctly. Additionally, it's important to ensure that the system is not triggered by non-security-related factors, such as pets or environmental conditions.
Video verification of alarms can significantly reduce instances of false alarms. Read more about video-verified alarm services.
Most modern alarm systems have features that can alert the designated users or the monitoring center if there is an issue with the control panel or any of the alarm devices. Some common features include:
- Supervision Signal: Alarm systems can be programmed to send a "supervision" signal to the monitoring center at regular intervals. If the signal is not received, the monitoring center will know that there is an issue with the alarm system.
- Tamper Detection: Many alarm systems have tamper detection features (also known as “Smash and Crash”) that can alert the users or monitoring center if the control panel is tampered with or if any of the alarm devices are removed or damaged.
- Fault Monitoring: Some alarm systems have fault monitoring capabilities that can alert the users or monitoring centers if there is an issue with any of the alarm devices or if there is a fault in the wiring.
- Remote Monitoring: Some modern alarm systems have remote monitoring capabilities, allowing the business owner or monitoring center to monitor the status of the system and receive alerts via a mobile app or web portal.
If the power fails, an intrusion alarm system that relies on just the mains power will typically stop working. However, most modern intrusion alarm systems have backup power supplies, such as batteries, that can keep the system running for a period of time in the event of a power failure.
The backup power supply is designed to provide temporary power to the alarm system until the mains power is restored. The duration of the backup power supply depends on several factors, such as the capacity of the batteries and the amount of power consumed by the alarm system.
It's important to note that backup power supplies are not a permanent solution for power outages. If the power outage lasts for an extended period of time, the backup power supply will eventually run out, and the intrusion alarm system will stop working.
In addition to backup power supplies, some intrusion alarm systems may also have cellular or radio backup communication options that can be used to communicate with the monitoring center even if the power fails. These backup communication options are typically designed to work in conjunction with the backup power supply to provide a more reliable and robust solution in the event of a power failure.
To ensure that the intrusion alarm system continues to function in the event of a power failure, it's important to regularly test the backup power supply and other backup features to ensure that they are functioning correctly.
Related Services